Learn about what SOC stands for (Security Operations Centers)— and how businesses all over the world count on them as part of a managed security service to expertly handle threat detection and incident response.
A security operations center (SOC) is a centralized force making use of people, processes and technology to monitor and analyze (in real-time) an organization’s network security. A typical SOC will continuously monitor network traffic in order to detect, prevent and remediate cyber threats, all the while improving threat intelligence.
In other words, SOCs are a dedicated IT security team made up of security analysts, engineers and SOC managers employing a variety of monitoring tools to keep track of security incidents that occur within a network.
You can think of them as a team of expertly-trained IT security professionals, whose sole job is to act as the best line of defense against any and all malicious cyber threats that attempt to attack your network. The larger your network is, the more vital having a security operations center and an SOC team becomes.
What is the Purpose of Creating a “Security Operations Center”?
SOCs are usually created when an organization deals with enough secure data and information through its various servers and devices to warrant one. That way, if a cyber attack occurs, SOC analysts can employ various security tools, as part of their 24/7 monitoring service, to detect and remediate threats before bolstering the network’s defense against such attacks in the future.
This is exactly the key benefit to having an SOC in the first place. Without one, it would be next to impossible to sort through all the data that can be generated by even one organization — even if you had your own Security Information and Event Management (SIEM) software in place.
Without a Security Operations Center actively sifting through and monitoring all that data, cyber attacks could very easily pile up and compound to the point where your organization could be dealing with them at a rate slower than they’re occuring.
SOCs help businesses of all kinds close that risk gap and stay on top of threats to their vulnerable network environments.
What is it Like Working in a Security Operations Center?
As previously mentioned, Security Operation Centers are focused primarily on the day-to-day monitoring and analysis of an organization’s network environment. Rather than concentrating on creating security strategies or building security architecture, their primary function is to monitor the ongoing flow of data through a network so that they catch cyber threats as they happen.
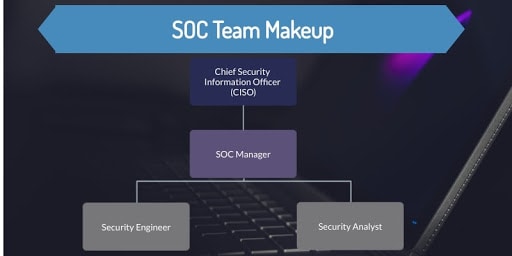
A Security Operations Center can include the following roles:
SOC Manager
This person manages the SOC team and reports to the Chief Information Security Officer (CISO). They oversee the team itself, lend guidance on technical matters and manage the SOC team’s financial activities in order to uphold their fiduciary responsibilities to the client.
Security Analyst
A security analyst is the first responder to any and all security incidents. They make sure that other staff members are properly trained so that they can implement correct procedures. They also work with other IT staff members and business admins to relay information about potential security issues and weaknesses.
When it comes to incident response, their method is usually rolled out in three stages:
- Threat detection
- Threat investigation
- Quick response
Security Architect/Engineer
This employee is responsible for maintaining the monitoring and analysis tools allowing the SOC to function at peak efficiency. They create and maintain the very security architecture the entire system is based on, and are typically software or hardware specialists.
Chief Information Security Officer (CISO)
The overall leader of the SOC, the CISO is not only the primary point of contact for an organization’s management, they are also responsible for defining the IT security operations of the organization itself. In essence, they captain the ship and take ultimate responsibility for the entire breadth of the organization’s IT security.
How Do You Efficiently Manage a Security Operations Center?
Focusing on the human element of an SOC first is widely regarded as the best approach to an effectively-managed Security Operations Center.
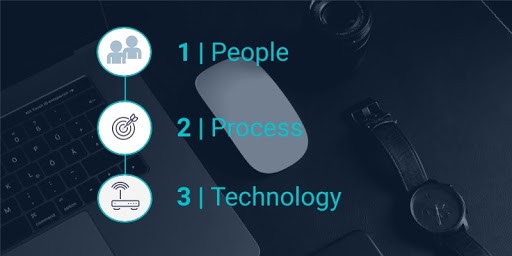
According the Infosec Institute, the process of best efficiency flows in the following order:
- People (team members)
- Process
- Technology
People: To run an SOC effectively, the first focus needs to be on hiring and training the right staff. These individuals are also required to keep up-to-date on the latest threat intelligence reports in the security community and use this information to constantly improve their detection and defense abilities.
Process: With so much data to sort through and so much room for error, implementing and sticking to defined processes that everyone follows is one of the best ways to ensure cyber threats are dealt with expediently.
Technology: Scripts and SIEM architecture are the bedrock of any organization’s IT network security. As such, the third area of focus for an SOC is on the technology side. As for what software is crucial for a Security Operations Center, the SIEM system utilized by the SOC will always be the cornerstone of the operation.
For any Security Operations Center to be truly effective, the structure of the team will ideally follow the outline above.
Summing up on Security Operations Centers
Now that you have more insight into what a SOC is, perhaps you still have some lingering questions. The various types of SOCs out there may lead you to ask: “what is a virtual Security Operations Center?” or “what is a global Security Operations Center?” and those are both excellent paths to lead you forward on your journey of SOC discovery. After all, the more you know, the better prepared you’ll be for whichever IT solution you hope to find.
If you’re interested in learning more about possible IT solutions that could help you, chat with us today.




